Navigating the ever-evolving world of technology can be quite the adventure, right? Especially now with Google & Yahoo email authentication requirements coming into play. As business owners, we’re already juggling a lot, and keeping up with tech’s twists and turns can be a challenge. It’s like they forgot we’re not all fluent in their tech-speak!
But here’s where having CyberCletch as your trusted partner comes in handy. We’ve always got our tech detective hats on, deciphering all the tech and its accompanying jargon for you. Whether we’re lending a helping hand or pointing you in the right direction, count on us to make your tech journey smoother.
The following instructions and information assumes you are using a custom domain for your company emails. For example, my custom domain is cybercletch.com, so my email looks like this: info@cybercletch.com. The following information does not apply to free email services like gmail, aol, verizon, or hotmail. If you’re sending marketing emails using a free email account; it’s time to upgrade.
Google & Yahoo Email Authentication Requirements – Why the Changes?
As we step into 2024, Google and Yahoo have rolled out new email authentication requirements, which marks a significant shift in our email marketing landscape. Other email providers are expected to follow suit. Our guide is for you if you are an entrepreneur needing to navigate these changes easily and understand the concepts quickly.
These new rules are to protect everyone from unwanted emails:
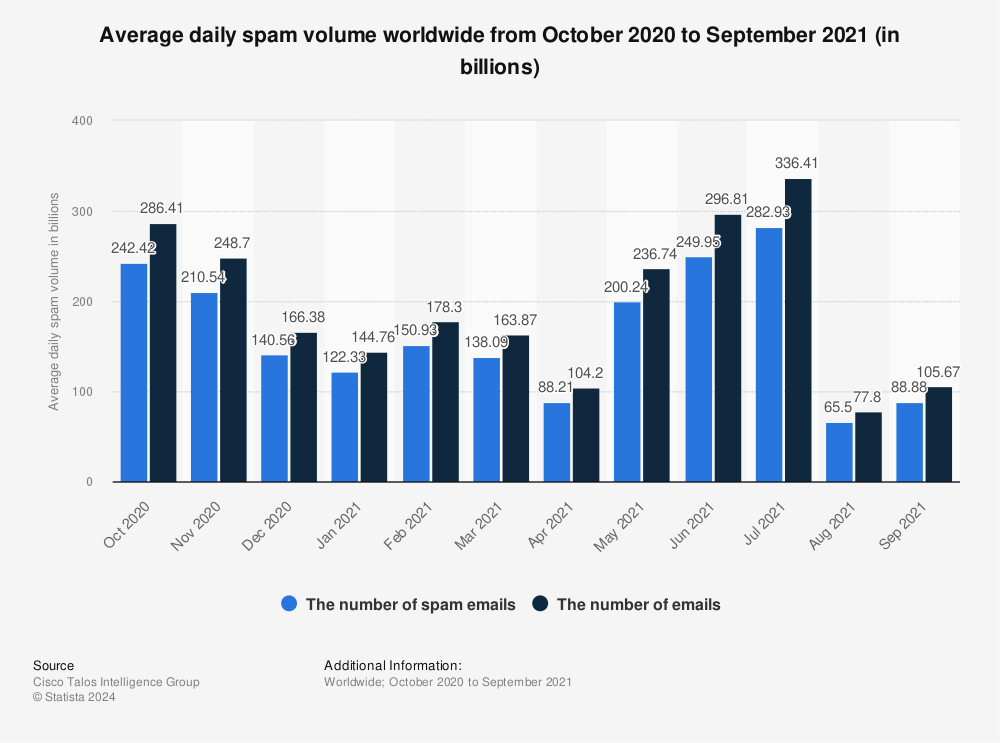
You can see from the chart above that spam emails are sent nearly as much as legitimate emails. These daily stats relate to emails sent worldwide but, according to Statista, the number one country targeted for spammy emails is the United States.
For business owners like you, these changes are more than just technical adjustments; they are a commitment to maintain credibility and trust in your client relationships. Proper email authentication now plays a crucial role in shielding your business from phishing attacks and ensuring your emails consistently reach your client inboxes.
How Does Email Authentication Work?
Email authentication is basically a digital passport for your emails that ensures your credentials are genuine and not forged. It involves several protocols like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
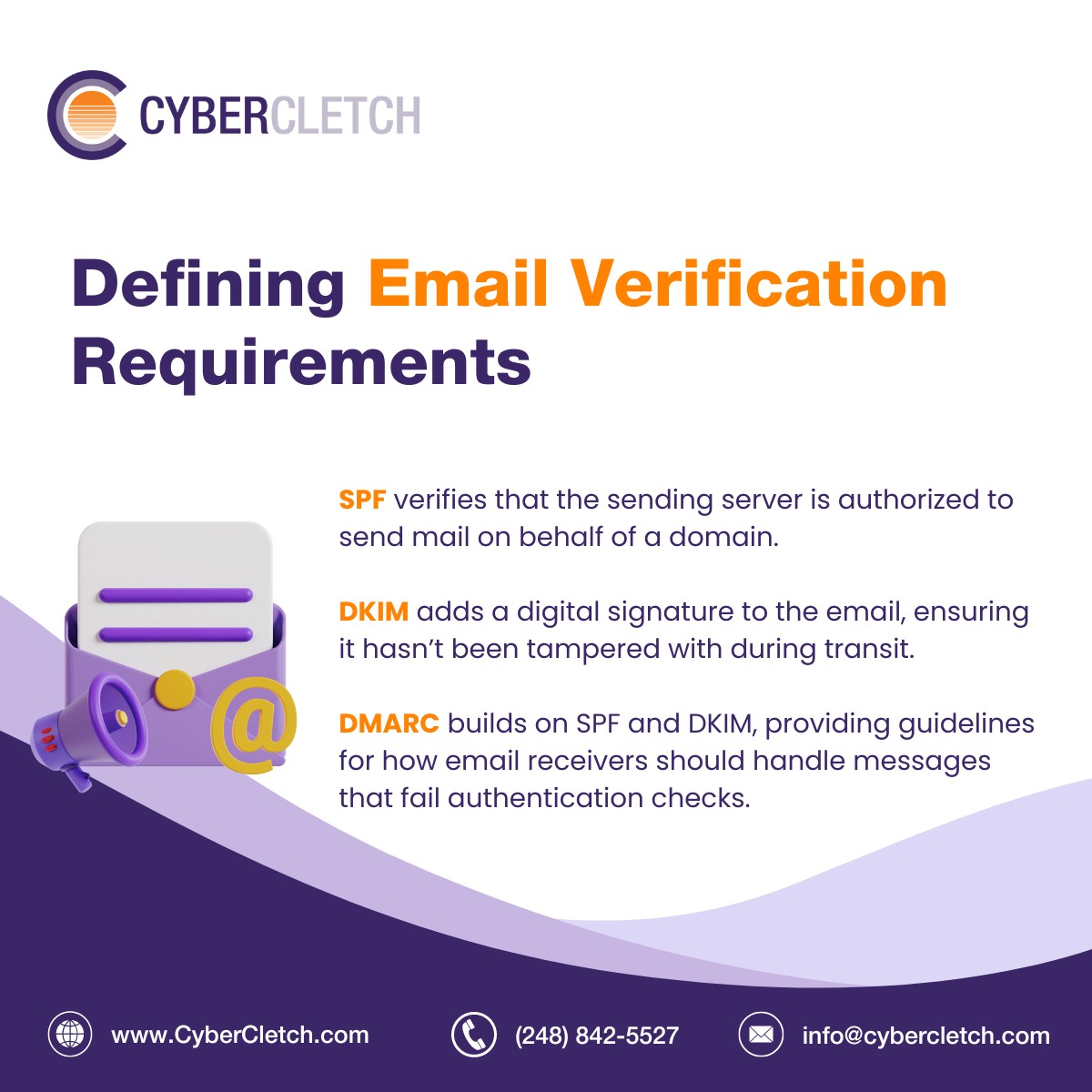
All three protocols work to improve the quality and accuracy of wanted email that end up in our inbox.
Impact of Email Authentication on Email Marketing
Legitimate email marketers should adhere to these authentication protocols to ensure their messages land in their targeted inboxes. Failure to set up Google & Yahoo email authentication requirements may result in emails being marked as spam or not delivered at all.

Expect other email providers to follow suit in the coming year.
How do I Meet Email Authentication Requirements?
At this point, the process might confuse laypeople. You must authenticate every location from which you send emails, including Gmail, Outlook, Constant Contact, Mailchimp, or your WordPress site.
How to Set Up Your Email SPF Records
Establish SPF records for your domain as a critical first step to authenticate your email communications and protect your brand from spoofing and phishing attacks. SPF allows you to specify which mail servers are permitted to send email on behalf of your domain, thereby improving your email deliverability and trustworthiness.
Here’s a straightforward guide to setting up your SPF records:
1. Identify Your Sending Sources:
Begin by compiling a list of all the services and IP addresses that send emails on behalf of your domain. This list may include your company’s internal mail servers, third-party email service providers (ESPs), and any other systems that send emails, such as CRMs or marketing automation platforms.
2. Create Your SPF Record:
An SPF record is a TXT record within your domain’s DNS settings. The record lists all the authorized sending sources for your domain. A basic SPF record might look something like this:

In this example, v=spf1 initiates the SPF record, ip4:123.456.78.9 authorizes an IP address, include:spf.provider.com allows emails from a specified domain, and -all indicates that emails from any other sources should be rejected.
3. Publish Your SPF Record:
Access your domain’s DNS management interface, usually provided by your domain registrar or hosting service. Create a new TXT record with the value you’ve constructed. The host name should be set to @ or your domain name, depending on your DNS provider’s requirements.
Finding DKIM Info
In most cases, your email sending platforms will ask you to publish a Domain Keys Identified Mail (DKIM) record that will automatically authenticate emails sent via their platforms from your domain.
Each of your email sending platforms should provide you with Domain Keys to input into your DNS. Go to each platform used and search “email authentication” in their knowledge base. Once you understand how to get the information specific to their platform, you’ll input it into your DNS.
For the Beginner:
Once you have the information from the services you use for sending emails, go to the website where your domain name resides. Within their control panel, you should have access to your Domain Name Servers, or DNS. This is where you add the information your email sending platforms provide. Most offer excellent directions for adding TXT and CNAME records.
For example, here is Constant Contact’s instructions.
(If you’re interested in a discounted Constant Contact account, just let me know!)
Once you’ve configured the DNS, it’s essential to test for accuracy since any misconfiguration can negatively affect your deliverability!
Testing your Email Authentication Requirements
Run tests to confirm your DNS settings are correct. You can put your work to the test with various online tools available for this purpose. Consider MX Toolbox or exploring others that suit your needs.
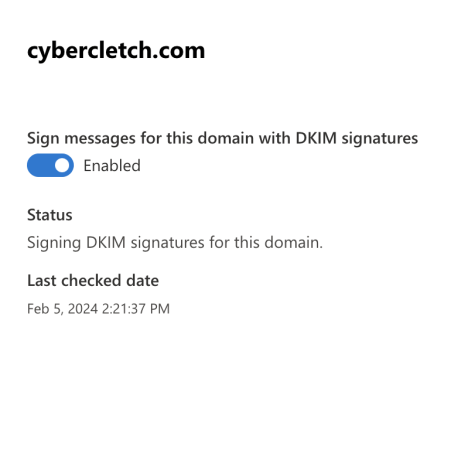
I gave Easy DMARC a shot and discovered my Outlook email wasn’t authenticating with my domain; instead, it was authenticating with cybercletch.onmicrosoft.com.
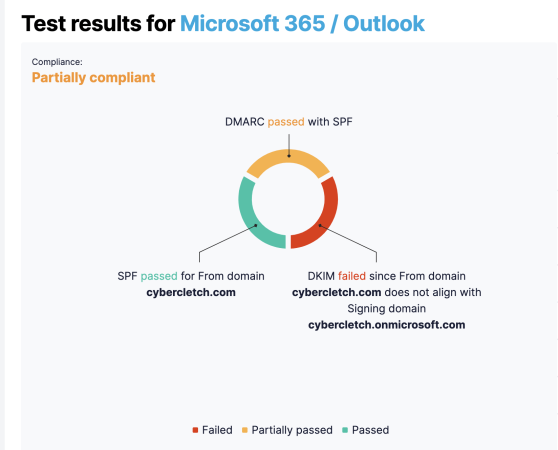
With a quick search, I discovered how to update Office 365 settings so my custom domain would be used for authentication instead. (For those navigating the Office 365 admin panel, you can try this direct link when you’re logged in!)
Easy DMARC provides a convenient way to test email deliverability across different platforms using unique email address identifiers. You can check out my first and second tests below as examples.
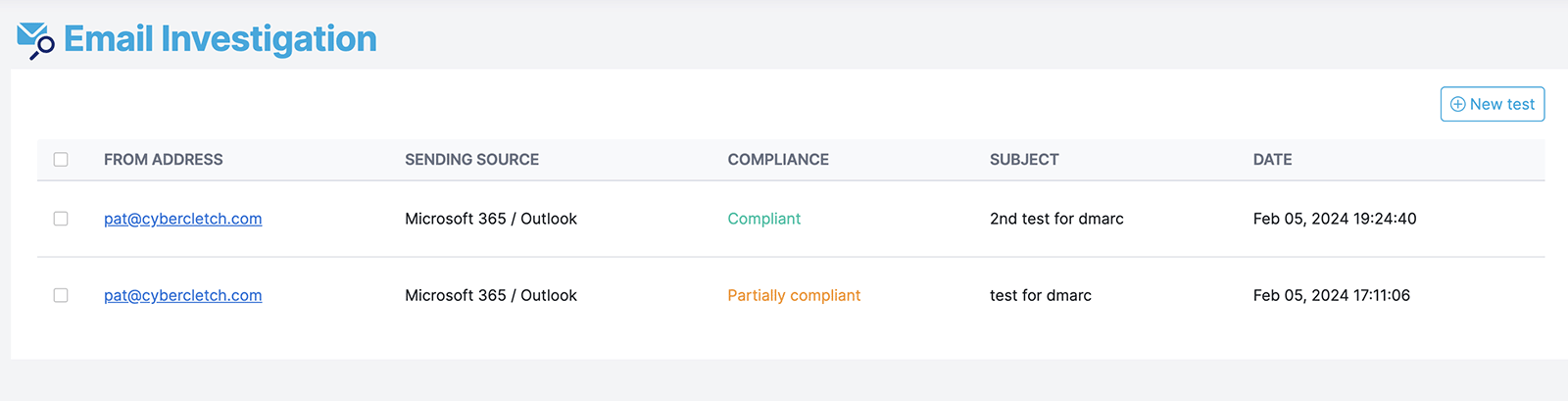
Be sure to test each platform from which you send emails to guarantee successful email verification. Easy DMARC offers a 14-day free trial, and it seems to remain free if your monthly email volume stays under 1000.
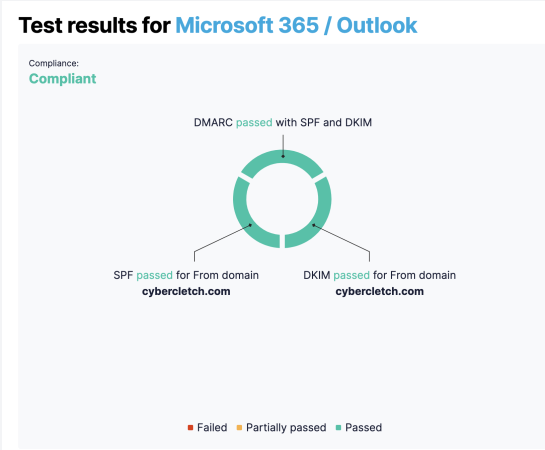
For WordPress Users: If you’re using WordPress for your website, several plugins can simplify the implementation of SPF, DKIM, and DMARC but you should still ensure these are correctly configured. Do a search in the WordPress plugin marketplace.
Best Practices for Email Senders
- Implement SPF, DKIM, and DMARC: Ensure your email sending infrastructure is set up with these authentication mechanisms.
- Regularly Monitor DMARC Reports: DMARC provides reports on authentication results. Regularly monitoring these reports helps you identify and rectify any issues. Typically there is a cost associated with this, but if you are sending a large volume of emails regularly, it’s a worthwhile investment.
- Gradual Implementation: If you haven’t implemented these protocols, start gradually to avoid disruptions. Begin with SPF, then DKIM, and finally DMARC.
Email authentication might sound technical, but it’s a critical step in ensuring your emails are recognized as legitimate. The DKIM, SPF, and DMARC tools are your allies in this process. Configuring these allies on your domain isn’t just about compliance; it’s about protecting your brand’s reputation.
Elevating Your Sender Reputation Beyond Email Verification
In the realm of email marketing, bolstering your sender or brand reputation transcends mere compliance with email verification standards. Here are two more pivotal strategies to focus upon:
1. Elevate Spam Prevention Efforts:
Maintaining a spam complaint rate under 0.3% is not merely advisable—it’s imperative. This benchmark rate demonstrates the importance of:
- Firstly, Understanding Your Audience: It’s essential to tailor your content to align with your audience’s preferences, which guarantees both relevance and engagement.
- Secondly, Monitoring Key Metrics: Keeping a vigilant eye on email delivery rates, open rates, and spam complaints is crucial. This oversight ensures you’re on top of your email campaign’s health.
- Thirdly, Managing Email Bounces: Aim to maintain your email bounce rate below 3%. This effort is vital to preserving your esteemed sender status.
- Next, Optimizing Email Frequency: Finding the right balance in how often you send emails is key to preventing recipient fatigue. Too much, and you risk overwhelming them; too little, and you may be forgotten.
- Furthermore, Upholding Reputation: Dedicate efforts to maintaining outstanding IP and domain reputations. A good reputation significantly boosts your email deliverability.
- Regarding List Hygiene: Implementing double opt-in procedures, engagement filtering, and establishing a clear sunset policy are pivotal steps to fostering a healthy email list.
- On Setting Clear Expectations: Make use of sign-up forms to clearly and transparently communicate what subscribers can anticipate, setting the stage for a transparent relationship.
- Concerning Personalization: Strive to deliver content that personally resonates with your audience, thus deepening engagement and fostering a connection.
- Finally, Simplifying Opt-Outs: It’s imperative to ensure every email includes an easily accessible, one-click unsubscribe option. This practice not only aligns with best practices but also honors your recipients’ preferences, respecting their choice to opt-out.
2. Embrace Regulatory Changes for Superior Deliverability:
Be sure to view regulatory updates as opportunities to refine and enhance your email marketing approach. This perspective shift, from obligation to improvement, can revolutionize the safety, security, and effectiveness of your email communications, laying a solid foundation for your business’s growth and success.
In Conclusion of Email Authentication Requirements:
As an email marketer, proactive engagement with these email authentication requirements and reputation-building measures is non-negotiable. If necessary, consult with your email service provider or a tech support team to ensure compliance and optimize your strategy.
In an era marked by heightened cyber threats, solid email authentication practices are crucial for building trust with your audience. By meeting these updated standards, you not only align with the expectations of major email platforms like Google and Yahoo, but you are also contributing to a safer, more reliable email ecosystem.
Remember, adaptability is the sign of a resilient business. Adopting these practices will enhance your email deliverability and solidify your reputation as a trustworthy and attentive brand. If you’re feeling overwhelmed by these technical requirements or need support in their implementation, don’t hesitate to reach out. CyberCletch is dedicated to helping ensure your business’s prosperity in the digital age.
CONNECT:SHARE:
