In the developing trend of cloud computing, companies everywhere are transferring their services to cloud servers in order to make their services and data available to multiple devices per user account. Google operates entirely on cloud, while other companies, such as Apple, are pushing for users to utilize their cloud services to host their data. This allows for these services to be accessible from a number of mediums, like the user’s computer, tablet, or phone, and it gives unparalleled convenience in data access for those who use it.
However, even the smallest security vulnerability allows for the entirety of this data to be accessed.
In this article by Mat Honan of Wired.com, Honan describes how crackers were able to first break into his Apple and Amazon accounts and use that information to get into his Google account. From there, the crackers had carte blanche into the rest of his digital information, shutting off and wiping his iPhone and MacBook, in addition to defacing his Twitter page.
While he was able to get in contact with the responsible parties, Honan lamented the fact that it was his own carelessness that led to the digital “nuking” of his online identity.
Unfortunately, the vulnerabilities in the systems of both Apple and Amazon have not been fixed as of yet, but there still is hope for Google users, as they have introduced a “Two-Step Verification Process” available to all accounts.
This additional security measure links your Google account to your phone and sends a six-digit security code via SMS or through an application for smartphones, which is then entered through the desired log-in bar. Standard messenging rates still apply, and the desired phone must be able to receive SMS messages from Google. The security benefits to this are astounding, as crackers would only be able to access your account fully if they physically got a hold of your phone.
Compatible services are detailed on the Google page for the process, and setup for the service itself is extraordinarily easy.
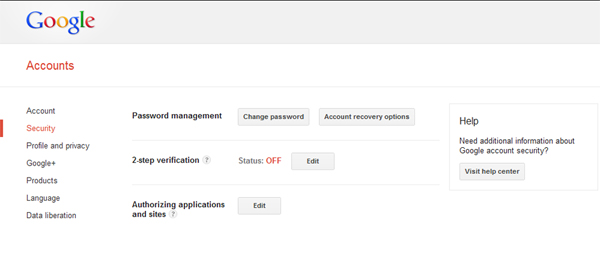
Once logged in to Google, enter into the “Account Settings” page, where various options are listed on the left-hand side of the screen. When you are there, click the “Security” link. You are then shown the Google security page, where the “two-step verification status is shown in the middle option:
Once you click “edit,” there is a simple four-step setup process in which you enter in your preferences and contact details so that Google can add your phone to the additional security verification.
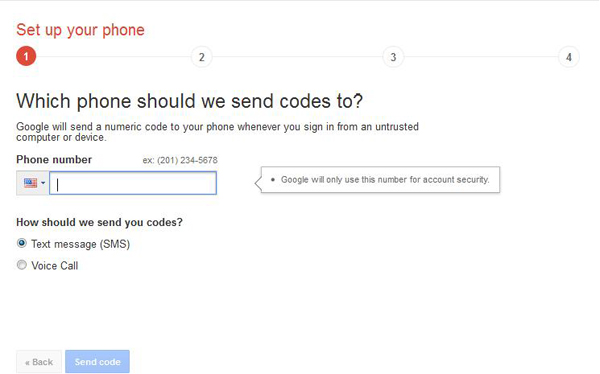
From the first step, you simply enter in your the number of your phone to be used, and select whether you desire to receive messages via SMS or voicemail:
Once your number is entered in, Google will send a six-digit code to your phone, after which you will enter into the site to verify. Once verified, Google will ask if the device you are entering from is to be trusted, which means that you will be able to log into Google services without the additional code solely from that device. This setting is adjustable through account settings in case you need to switch trusted devices.
After you have selected this, you will be prompted with a final screen in which you can turn on the two-step verification for your desired account. In case of a lost phone, you can edit the number, again through the account settings page.
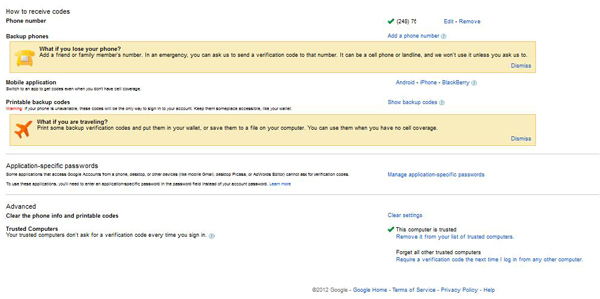
Now that you are officially verified, you will redirect to the settings page, where you can change any settings that you wish, including the ability to print out access codes in case of lost mobile coverage while traveling, etc.:
If you do not need to change anything, you have completed the process! You will now be prompted with the code screen when logging in from any unrecognized device.
As wonderful as this additional security can be, it is always advisable to take any additional measures to secure any other accounts. This site from Microsoft details how to create passwords that are harder to crack, and daisy-chaining multiple accounts will allow possible hackers to more easily gain access to your online resources, so vary your login information!
In the digital age, quite a bit of information can be gained through these security exploits, so use any knowledge you have in order to protect your networked identity!
CONNECT:SHARE: